Trusted PCIDSS Audit & Certification service provider across Globe.
End to end PCIDSS Audit & Certification services, Get compliant faster with our experienced QSA Team.
All entities, including merchants, service providers, and financial institutions, must complete a quarterly scan to maintain compliance with PCI DSS. By using GTISEC, businesses can scale more quickly, reduce costs, and realize other hidden efficiencies.
Quantitative analysis validates our competence.
We provide enterprises across the world, the ability to safeguard operations through cost‑effective, high‑impact security solutions
50+
Countries with our footprint
1200+
Clients in diverse sectors
700+
SAQ merchants supported
900+
Level 1 PCI Certifications provided
The Audit Experience Simplified.
Fortify your digital infrastructure with our military-grade security platform. Transform complex compliance into streamlined, intelligent protection.
Hall Of Fame
Deep roots in compliance leadership with years of experience securing enterprise merchants and financial institutions.
Understand Your Risk Posture
Comprehensive baseline risk assessment tailored to meet multiple compliance frameworks across industries.
Minimize Vendor Risk
GTISEC solutions enable rapid scaling while reducing costs and uncovering hidden operational efficiencies.
Address Emerging Threats
Proactive threat intelligence and adaptive security measures to counter evolving cyber risks.
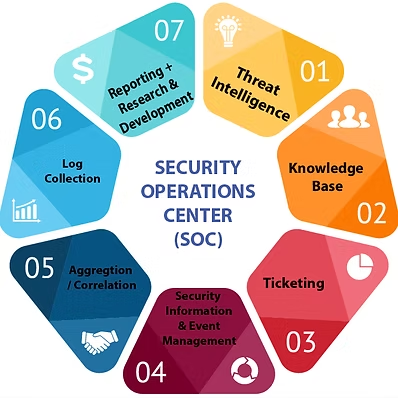
Enterprise-grade SOC Monitoring Excellence
Protecting your infrastructure with continuous vigilance and rapid threat response
24/7
Real-time threat monitoring
15+
Minutes average incident response time
99.9%
Uptime SLA guarantee
10k+
Security events analyzed daily
Get Started Today
Request a Quote
Ready to secure your business with professional cybersecurity services?
Our expert team is here to help you choose the right solution for your needs.
What you'll get:
- ✓ Personalized consultation
- ✓ Detailed proposal
- ✓ Competitive pricing
- ✓ Expert guidance
Not sure what service you need?
Our experts will help you choose the right solution.
Contact Us for More Information.
Contact Us for More Information.
Quick Quote Request
Fill out the form below and we'll get back to you soon.
What Our Clients Say
"Partnering with GTIS for PCI DSS compliance was invaluable. Their expertise and support ensured a smooth journey to achieving stringent security standards, highly recommended."